In today’s market, organisations seek to instil confidence in their clients and demonstrate their commitment to ensuring the security of the information they manage. To do this, having certification of an ISO standard or regulation relating to security offers a competitive advantage, as it shows that the organisation correctly manages its security requirements in information processing processes.
Cybersecurity and ISO standards
Cybersecurity is really booming these days, but why is this? The growing number of security incidents and attacks relating to information and IT systems that organisations are experiencing mean that the need for controls to guarantee the security of devices, communication networks and information assets is indisputable. It is from this need that the concept of cybersecurity arises.
The aim of these types of attacks is to access, modify or destroy sensitive information belonging to organisations.
The implementation of effective cybersecurity measures is not an easy matter because due to the large amount of equipment and technologies used, the cybercriminals always manage to find new ways of carrying out their attacks. However, there is a way of implementing data and information protection measures that makes the procedure for implementing these IT security measures somewhat more straightforward and natural.
These are the ISO standards and regulations relating to cybersecurity and information security. ISO standards are developed and published by the International Standards Organisation (ISO). Both ISO and the IEC (the International Electrotechnical Commission) are the leading specialists in standardisation globally. Through technical committees formed of member organisations of both ISO and IEC, they devise international standards drawn up to standardise specific processes in areas such as information security.
Today, these standards constitute an indispensable element of the compliance systems of organisations, bringing them prestige and international recognition. The differential value that the implementation of ISO standards offers organisations, compared to their competitors, is due to the fact that these certified standards are reviewed and audited periodically to ensure compliance, which considerably improves the standing of the organisation in the eyes of stakeholders such as clients and shareholders.
ISO standards are numbered incrementally based on the area they address and are divided into families, grouping those that relate to similar issues together. The aim of these standards and regulations is to identify techniques, policies, guidelines, skill-building, etc. in relation to the area they address (security, continuity, and quality, etc.).
ISO 27000 Family
The ISO standards include the ISO 27000 family. This is a series consisting of various information security standards that set out guidelines and requirements for implementing an Information Security Management System (ISMS) with the aim of managing information security within an organisation.
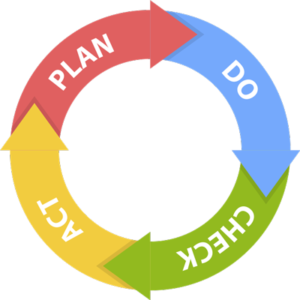
Within this set of standards, the main one is ISO 27001, the benchmark standard for the whole series. This standard sets out requirements for the establishment, implementation, maintenance and continuous improvement of an ISMS. The process of continuous improvement is based on the Deming Cycle or PDCA (which in English stands for Plan-Do-Check-Act) .
The rest of the standards in the family serve as a guide and help for implementation of the ISMS. Another noteworthy standard is ISO 27002. This is a guide to best practices that describes the control objectives and controls required with regard to information security.
From the same family, and with a more specific aim, is ISO 27031. This is a non-certifiable standard that serves as a guide and provides a series of methods and procedures for establishing aspects that lead to an improvement in the preparation of an organisations’ ICTs to guarantee and consolidate business continuity. That is to say, the main objective of this standard is to ensure the continuity of services and ensure that the organisation can get back on track when faced with a disaster situation, re-establishing a previously agreed operational state.
Similar to the above standard is ISO 27701, also from the ISO 27000 family. This also establishes requirements for administering, managing and protecting the company’s personal data privacy, based on regulations and legislation such as the GDPR (General Data Protection Regulation). Based on the requirements, controls and objectives of the ISO 27001 security standard, it includes guidelines for protecting the privacy and confidentiality of personal data handled by a company. It should be pointed out that this standard is achievable only in conjunction with ISO 27001 certification.
Other regulations and standards
In addition to the above-mentioned ISO standards, there are many other standards relating to the world of cybersecurity.
One clear example are the NIST standards, the National Institute of Standards and Technologies, a technology administration agency that is now part of the US Department of Commerce. The standards that it develops include, for example, SP 800-53. The SP 800-53 standard offers a list of controls that support the development of secure and resilient federal information systems. These controls serve as guides and standards for both operational and technical standards used by information systems to maintain the security of the information.
On the other hand are the so-called Service and Organisation Controls 2 (SOC 2). This is an international standard for reports on the cybersecurity risk management systems of organisations produced by the American Institute of Certified Public Accountants (AICPA). These reports detail the controls that an organisation implements in their system relating to security.
There are two different types of SOC 2 report. The first SOC consists of a one-off evaluation. That is to say, an evaluation is carried out at a particular moment with the aim of determining whether the controls implemented by the organisation have been properly designed and are appropriate, taking into account the requirements that need to be met.
With regard to the second type of SOC 2, this consists of a more long-term evaluation, which generally covers a period of about one year. In these kinds of reports, the controls the organisation has in place are evaluated over the agreed period of time to determine if they have been designed correctly and that they function properly throughout the evaluation period.
At a national level, there are guides, regulations and instructions on security that have been developed by the CCN (National Cryptological Center). These seek to protect the security of organisations and increase the level of cybersecurity. The series developed are mainly focussed on Public Administrations.
Also worth noting in this article is series 800. This series is related to the National Security Framework (ENS), as they provide procedures for the correct implementation of the measures and requirements featured in the series.
We should also mention both the COSO model and the COBIT standard. COSO (Committee of Sponsoring Organizations of the Tradeway Commission) is an organisation consisting of private bodies based in the USA, which is dedicated to providing a common guidance model for organisations on fundamental aspects of executive management and governance, business ethics, internal control, business risk management, fraud control and the provision of financial reports. As for the COBIT standard (Control Objectives for Information and related Technology), this is a set of best practices for companies for the management of information systems.
At GlobalSuite Solutions we offer help and advice to all kinds of organisations and sectors on implementing the Management Systems required by these standards. We also have the GlobalSUITE® software that, developed by our team, is a tool that enables the implementation, management and maintenance of the requirements demanded by each of the different ISO standards.






