Transform your company’s information security management with GlobalSuite® Information Security, the end-to-end solution designed to automate and optimize ISO 27001 compliance. This specialized software makes it easy for you to implement, manage, and maintain Information Security Management Systems (ISMS), ensuring that you meet the most demanding standards in an affordable and intuitive way. With GlobalSuite®, you not only simplify the complexity of the ISMS, but also improve the protection of your most valuable assets.
Our software
Information Security
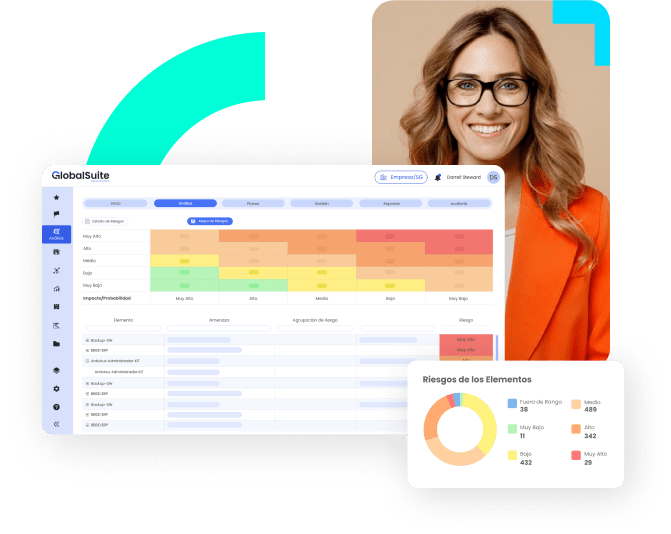
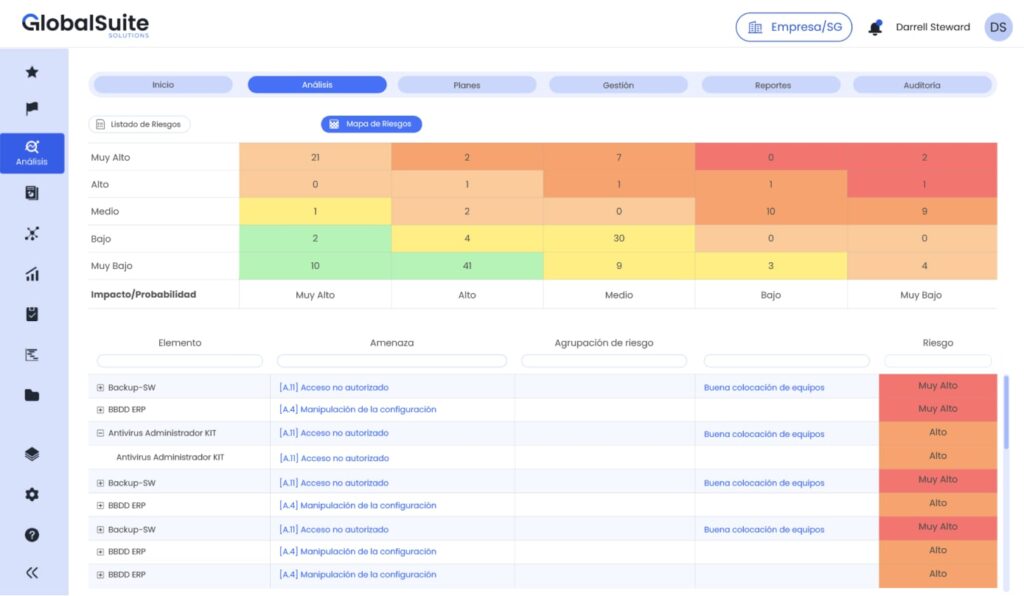
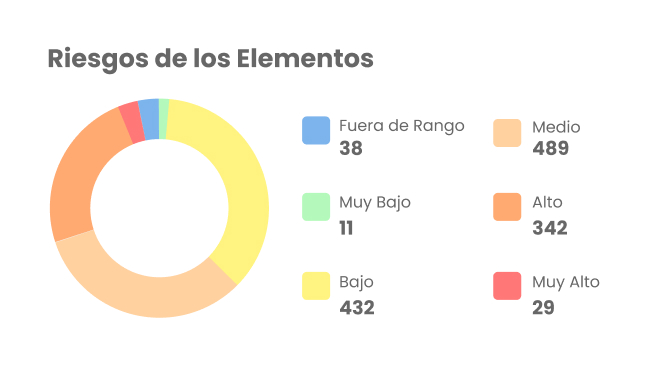
ISO 27001:2022 offers organizations a robust methodology for assessing and mitigating risks, implementing effective controls that strengthen security and ensure business continuity. GlobalSuite® guides you through the Plan-Do-Check-Act (PDCA) cycle, from the initial analysis to the final audit, ensuring efficient and professional management at every step.
Elevate your competitive advantage with GlobalSuite®. It facilitates the ISO 27001 certification process, optimizing your operations by centralizing regulatory compliance, reducing manual workload, and improving your organization’s operational efficiency.
Strengthens cybersecurity
It provides a solid foundation for cybersecurity, protecting your business against internal and external threats, and improving overall resilience.
Centralized compliance
Efficiently manage compliance with multiple regulations and security requirements, keeping your business up to date with the latest regulations and simplifying administration.
Operational efficiency and cost savings
It automates repetitive processes, reducing manual workload and operational costs, allowing you to focus on strategic activities.
Everything you need in
A single solution
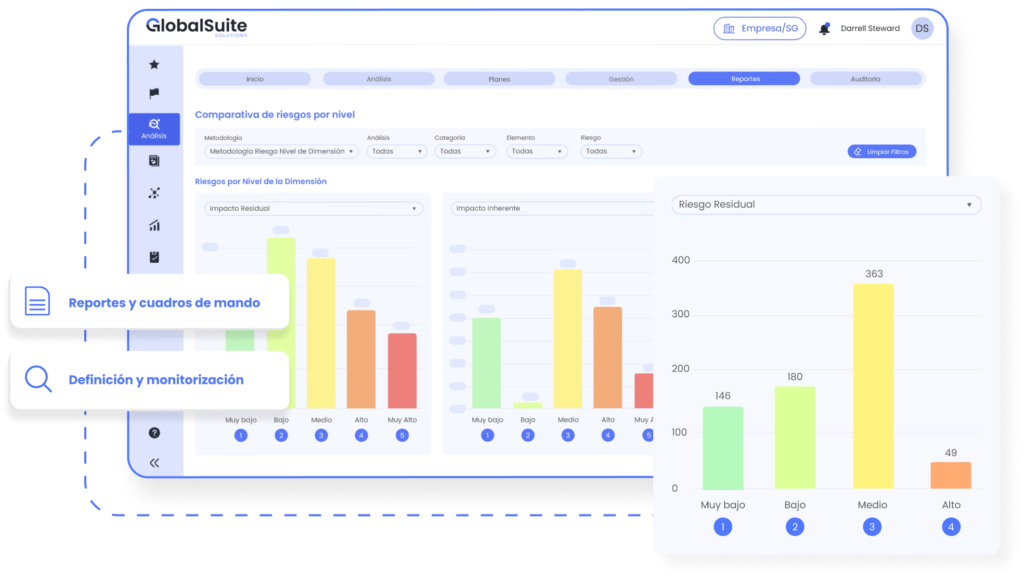
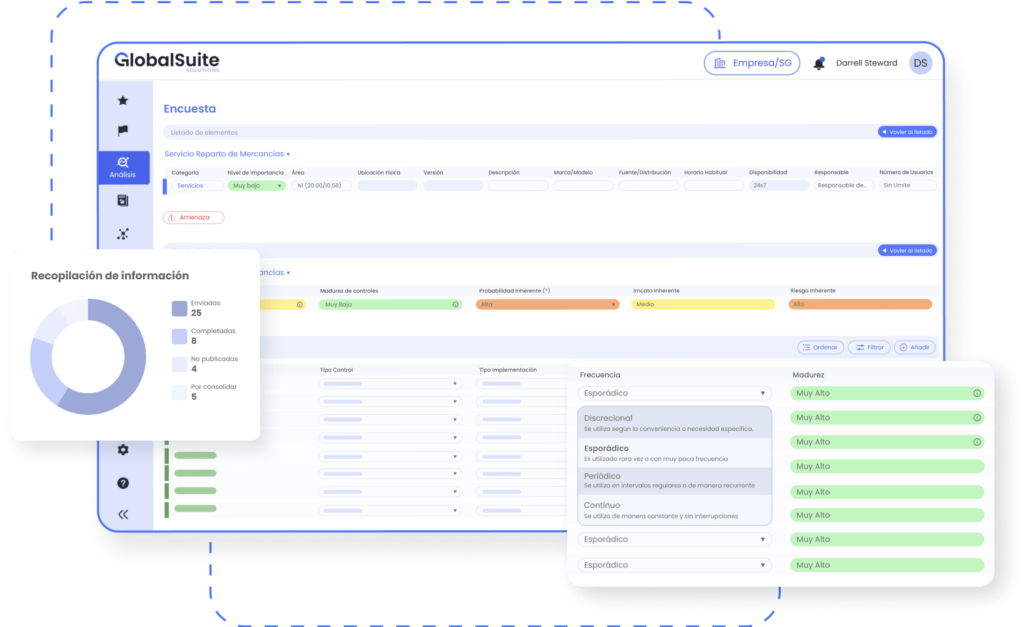
Take control of your operation
with a powerful and flexible solution
It integrates and centralizes controls and risks dispersed between Security, IT and Compliance areas, improving the cohesion and effectiveness of management.
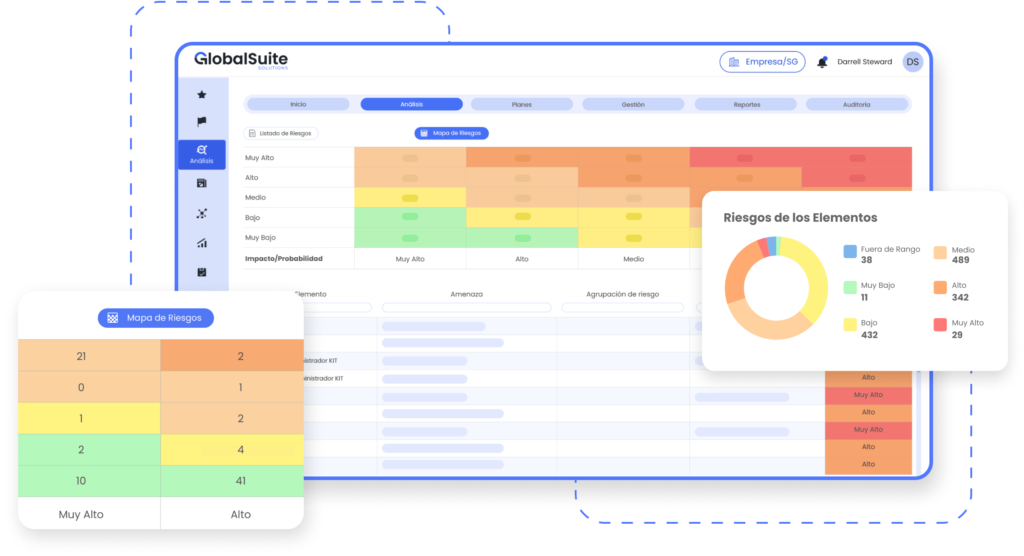
It offers customizable incident management with workflows, real-time risk assessment, and plans for continuity, capacity, and availability. It includes continuity test scheduling, non-conformance and corrective action management, supplier evaluation, and SLA management.
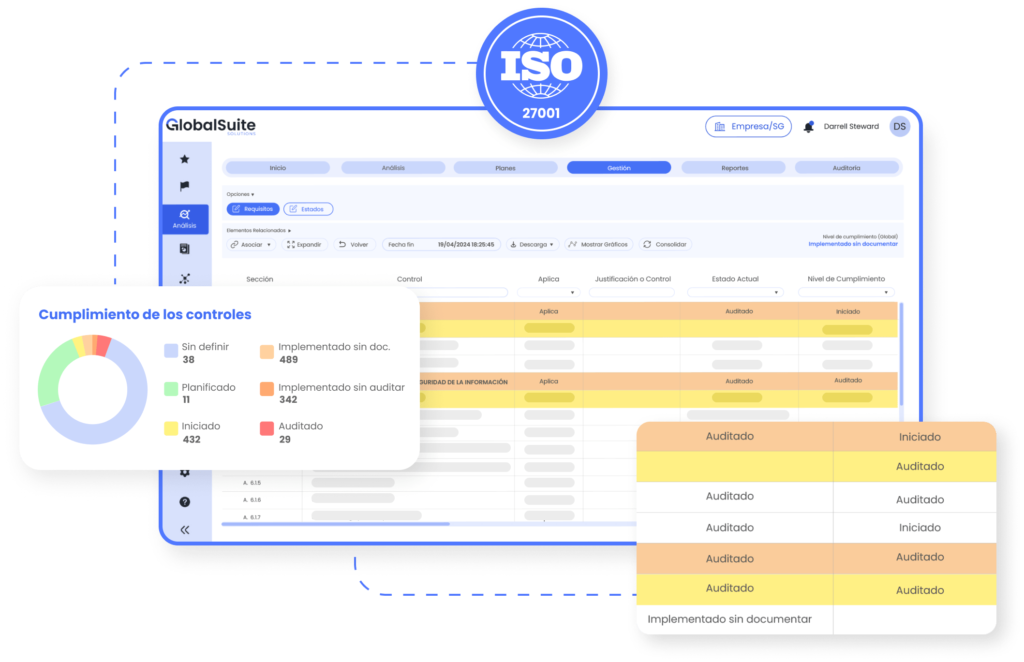
It enables efficient document management, ensuring document organization, quick access, and regulatory compliance. It includes features such as version control, access permissions, and secure storage.
Guidance of services and processes through asset inventory. Setting up dimensions and valuation levels.
It incorporates the full power of artificial intelligence to improve accuracy in data analysis, automate repetitive tasks, and provide advanced risk and control recommendations.
Automate repetitive and critical processes, reducing manual workload and improving operational efficiency. This allows you to focus on strategic activities and better manage safety regulations.
Comprehensive Solutions
Consulting and Auditing
We offer comprehensive consulting and auditing services to implement, audit, train, advise and certify all types of companies and organizations. With more than 2,000 projects implemented, we ensure a comprehensive and personalized approach that guarantees success in your project. We work with a wide range of standards and standards, including ISO 27001, ISO 31000, ISO 22301, ISO 9001, ISO 20000, ISO 14001, ISO 45001, ISO 50001, ISO 27017, ISO 27018, GDPR, ENS, among others. Complete your project with expert consulting.

Turnkey projects
We facilitate a quick and hassle-free implementation, allowing your organization to get the management system up and running efficiently and without interruptions. We take care of all the technical and configuration aspects, including automatic migration of information, so you can start working without delays or inconveniences.

Accompaniment and Training
We provide comprehensive monitoring of each project by a team of technical experts and consultants. We offer continuous training to ensure optimal knowledge transfer, ensuring that your team acquires the necessary skills to maintain and improve the management system in place.

Soporte
Continuous support service in Spanish, to ensure that your organization always has the necessary assistance. Our team of experts is available to answer any questions or problems, ensuring the optimal functioning of the management system.

Success stories
Industry: Manufacture of sealing systems for automobiles.
Size: +1000 employees
Zone: Spain
Products: Data Protection, Security and Whistleblowing Channel
Main regulations: GDPR / ISO 27001 / Whistleblowing Channel